

|
Date Time Time table 3F Main hall 2F Room 201,202,203,204 26, October (Mon) 13:00-14:20 A1: Access Log (1) CSS2009 B1,C1,D1,E1,F1 Session 14:35-15:55 A2: Access Log (2) CSS2009 B2,C2,D2,E2,F2 Session 16:10-17:00 CSS2009 Inviete Session (1) 17:20-18:00 MWS Cup 2009 18:10-20:40 27, October (Tue) 8:30-9:50 A4: Captured Data (1) CSS2009 B4,C4,D4,E4,F4 Session 10:05-11:45 A5: Captured Data (2) CSS2009 B5,C5,D5,E5,F5 Session 13:00-14:20 A6: Captured Data (3) CSS2009 B6,C6,E6,F6 Session 14:30-15:30 15:40-17:00 A7: Malware samples (1) CSS2009 B7,C7,D7,E7,F7 Session 17:15-18:15 CSS2009 Invite Session (2) 18:30-20:30 Social Event 28, October (Wed) 8:30-9:50 A8: Malware samples (2) CSS2009 B8,C8,D8,E8,F8 Session 10:05-11:45 A9: Malware samples (3) CSS2009 B9,C9,D9,E9,F9 Session 13:15-14:15 IWSEC2009 Invite Session (1) 29, October (Thu) 11:00-12:00 IWSEC2009 Invite Session (2)
A9-2: Shinsuke Miwa, Generate Activity Dataset using MAT; Minimal-attack/Malware Analysis Testbed
[Abstract] In late years a malware which became complicated by malicious attackers is used. Because the number of malware increases for an explosion, a burden of work centers on a person of limited analysis, and analysis becomes difficult. Therefore it is necessary to analyze a malware automatically. However, an action of a malware changes by practice environment. So precision of automatic analysis and efficiency deteriorate. Therefore, by changing of practice environment, precision of automatic analysis and efficiency are studied.
Manuscript in PDF(Japanese) |
[Abstract] Getting a dataset, which would be observed from activity of live malware and attacks, is difficult because when we would observe the dataset, we should use isolated sandbox to avoid adverse side effects from malware to the Internet. So, we have been developing "MAT" (Minimalattack/Malware Analysis Testbed), which is an isolated sandbox for analyzing malware with mimetic Internet. In this paper, we briefly describe design and implementation of "MAT", and also describe design and implementation of sequencer to generate activity dataset. Furthermore, we explain an activity dataset, which generated using MAT based on CCC Dataset 2009.
Manuscript in PDF(Japanese) |
A8-2: Kazuhiro Nomura, Analyzing Behavior of Malware by Virtual Machine Monitor
[Abstract] Due to bot's sophisticated techniques for hiding itself, it is difficult to distinguish the bot's malicious process from legitimate process. Hence it is quite essential for bot detection to find bot's inevitable behaviors. For almost all bots, intrusion into system directory and registration themselves to auto run list are key function which they should equip to stay alive themselves in PC. Therefore, a clever bot, which has both intrusion and attack behaviors and separate them according to the execution environment, will exhibit again its intrusion behavior as long as its environment is restored to pre-intrusion state. Needless to add, a naive bot, which simply iterates intrusion and attack behaviors, will always show its intrusion behavior. Therefore in this paper, we focus on this characteristic of "the repetitiveness of intrusion" as a bot's inevitable behavior and propose a bot detection scheme to utilize the characteristic.
Manuscript in PDF(Japanese) |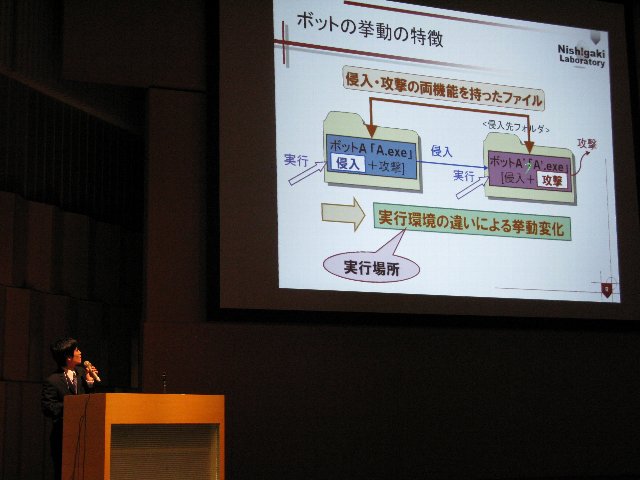
A8-3: Ruo Ando, A profiling method of malware's behavior using integrated virtualized system monitor
[Abstract] Technology of malwares progresses steadily, and new ones are appearing everyday. For provision against them, we need to analyze their behavior, and its results should be fed back to intrusion detection system and so on. Old-fasioned malwares can be analyzed by a disassembler or a debugger. But, recently, some ones are packed not to be analyzed easily. Some other ones have a mechanism for detecting a debugger, and they change their behavior when a debugger was detected. Even if they have such mechanisms, it is easy to analyze them from inside operating systems. However, actually, it is not easy from Windows because it is a proprietary software. To solve these problems, we are trying to analyze malware's behavior by hypervisor-based virtual machine monitor. In this paper, we discuss how to improve BitVisor to monitor malware's behavior on Windows.
Manuscript in PDF(Japanese) |
A8-4: Makoto Iwamura, Automatic Malware Classification System based on Similarity of Machine Code Instructions
[Abstract] In this paper a profiling method of malware’s behavior using integrated virtualized system monitor. Our monitor is API hook based which enables fine-grained inspection of resource accesses such as file, memory, socket and registry on Windows OS. In proposed system virtualization technology is applied to monitor guest VM without impacting its performance and utilization. In experiment we show some examples of profiling of malware.
Manuscript in PDF(Japanese) |
[Abstract] We propose an automatic malware classification system based on similarity of machine code instructions. Our classification system has three modules, which are the unpacker using customized page-fault handler, the probabilistic disassembler and the classifier based on a similarity of machine code instructions. Experimental results with the malware samples provided by Kyoto University and CCC DATAset 2009 malware samples show that our system can drastically reduce the quantity of reverse-engineering work to reveal the entire view of malware.
Manuscript in PDF(Japanese) |
A7-2: Takahiro Kasama, Malware Sandbox Analysis System with Accumulated Server Responses Collected by Dummy Clients
In this paper we propose an analysis of malware’s behavior using automated deduction system. In our system the extenal log of malware’s behavior is analyzed by FoL (First order Logic) based theorem prover. The some pattern to be discovered is describles as counterexample which deduced from log of Windows OS on which malware was executed. By proposed method we can find the patterns regardless of noise and specification of Operating systems and malicious softwares.
Manuscript in PDF(Japanese) |
A7-3: Kazufumi Aoki, Malware behavior analysis using semipermeable network
Many recent malware change their behaviors according to those of remote servers they interact, such as Command and Control (C&C) servers and file servers. Thus, it is important to carefully observe the changes of behaviors of these servers when malware sandbox analysis, in which malware sample is actually executed in a testing environment (i.e. sandbox) to observe its behavior, is conducted. However, keeping the malware active in an Internet-connected sandbox for a long time to observe its interactions with these servers involves a high risk that their attack may exit the sandbox as well as a high operational cost. In this paper, we propose a new malware sandbox analysis method in which we utilize a dummy client that interacts with the servers instead of a malware sample. The dummy client is automatically created from traffic log observed by sandbox analysis. Server responses collected by the dummy clients are then fed to the executed malware in the sandbox to observe its corresponding reactions.
Manuscript in PDF(Japanese) |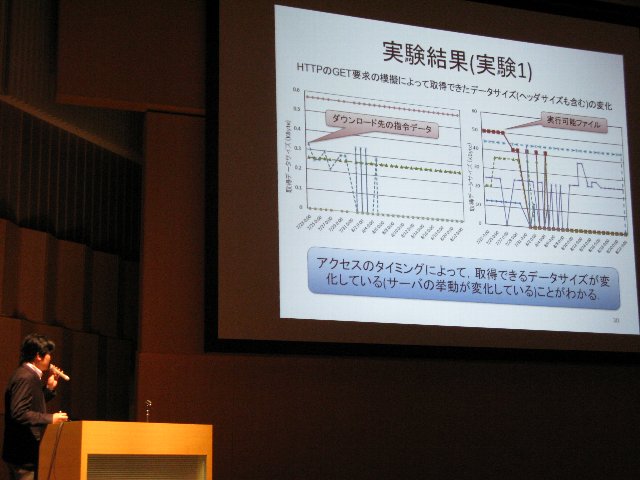
A7-4: Masayoshi Mizutani, The Implementation of an Environment to Collect and Analyze Malware Adapted to Various Infection Methods
Dynamic analyses which execute malware by the isolated environment cannot obtain an enough result. In this paper, we analyze CCC DATAset 2009 malware by Botnet Watcher, which use semi permeable virtual network. And we investigate amount of code which executed in isolated environment and semi permeable environment. Results shows that Botnet Watcher can obtain many destinations, additional execution binaries and can increase amount of executed code.
Manuscript in PDF(Japanese) |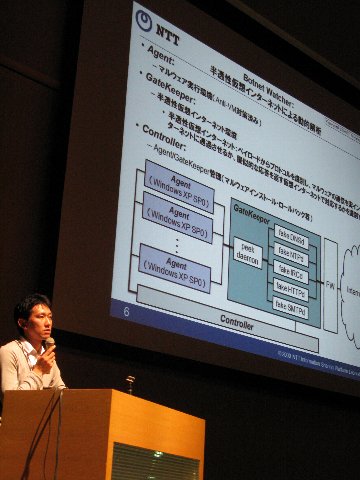
As malware (malicious software) activity patterns change, flexible collection and analysis of malware became necessary. Nowadays, most honeypots that are waiting for malware communications were used to collect their information, but these honeypots can't adapt to malware that infect computers over web browsers. This paper describes requirements of malware collection and analysis that can adapt to various infection methods, and this paper presents an implementation of malware collection and analysis environment that can change its structure and control its communications. Then, the results of dynamic analysis, which was done on malware that matched with hash values provided on CCC DATAset 2009, is also presented in the paper.
Manuscript in PDF(Japanese) |
A6-2: Kota Kisamori, Analysis of malicious traffic based on TCP fingerprinting
Recently, damage caused by the botnet becomes a big problem. There exists a problem that the other bot PCs can be produced, even if one bot PC could be specified and removed. Therefore, it is not a fundamental solution to specify only the bot PC.To solve this problem authors proposed the multistep trace back system. In this paper, the authors developed the second step system which consists of two methods: first method is to use the black list of the C&Cserver and the second one is to use analytical result using quantification methods No. 2 and CCCDATAset2009. In this paper, we describe the second step system using two methods and the result on the evaluation using CCCDATAset2009.
Manuscript in PDF(Japanese) |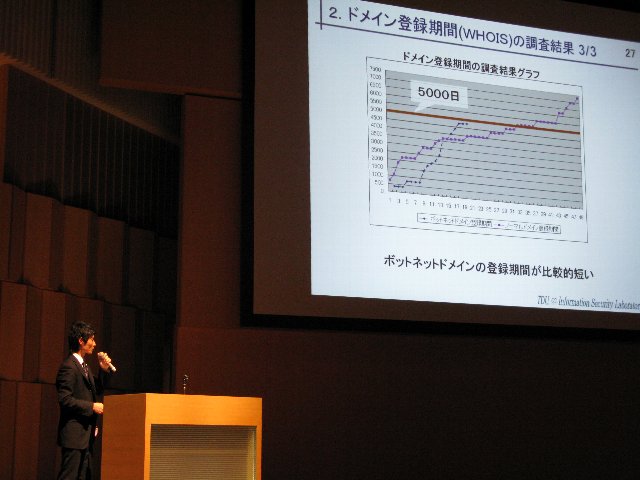
A6-3: Shigeki Kitazawa, Evaluations of A Targeted Attack Detection System
Modern full-kernel malware (FKM) such as Trojan.Srizbi is known to have its own network functionality and use it directly from kernel-mode for evasion purpose, concealing from recent alert tools. These network drivers tend to have its own implementation which exhibits intrinsic TCP fingerprints. We first attempt to extract FKM-possible TCP fingerprints using CCC (Cyber Clean Center) data sets, then we analyze traffic sequences which have frequretlyoccured source IP addresses. We then study the properties of the fingerprints and the activities of the hosts that are likely infected with FKM through the analysis of CCC data sets and other traffic data sets of several production networks.
Manuscript in PDF(Japanese) |
A6-4: Nobutaka Kawaguchi, Enhancing Network-based Bot Detection using Virtual Machine Introspection
Recently, the threat of "The Targeted attack" has become aggravated. The Targeted Attack is an attack that limits the attack target to a specific organization and the person. In the targeted attack, a user is made to execute the malware by the sleight of hand. Moreover, the evasion measures of Anti-virus software are often taken. Accordingly it is very difficult to take measures to the malware by Anti-Virus Software. In this paper, we propose the new Targeted Attack Detection Sysntem. Our system can detect network behaviors of the malware. We show that our system is very efficient to detect the behaviors of the malware by the real observed data(CCCDATAset2009).
Manuscript in PDF(Japanese) |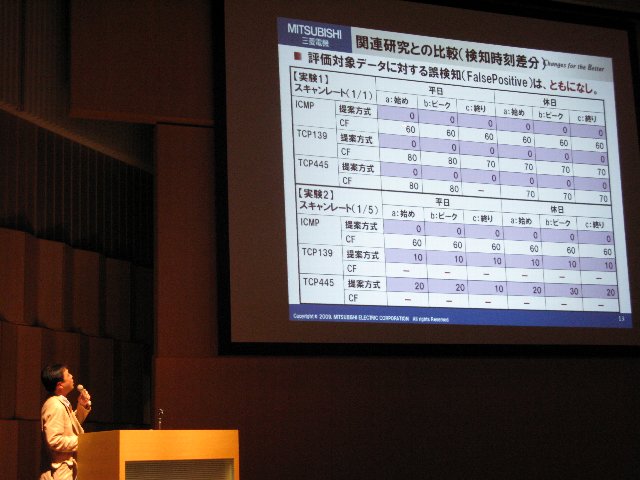
In this paper, we propose a bot detection method that combines traffic analysis by Network based IDS (NIDS) and process context information obtained from monitored machines by using Virtual Machine Introspection. Some existing NIDS determine a machine is infected if it is suspected of performing both of the Command and Control(C&C) communication and infection activities. This approach, however, has possibilities to generate false positives and negatives. For example, a machine that simultaneously runs two benign processes which perform C&C communication-like and infection-like activities respectively could be falsely detected. To address this problem, the proposed method enables NIDS to achieve process-grained detection by adding the context information of the processes that perform network activities. For example, this method declares a machine is infected when the machine has a process that appears to perform both of C&C communication and infection activities. Through experiments using a prototype implementation on Xen and a bot sample specified by CCC DATAset 2009, we confirm that the proposed method has a capability to detect bots appropriately.
Manuscript in PDF(Japanese) |
A5-2: Tatsuya Sakaki, A Proposal of an Analysis Method of malware communication by generating meta data
Damage by malware attack has been viewed with suspicion recently. So detecting infected PCs is necessary for the attacks. Against this background, we have studied the infected PC detecting method by comparing malicious traffic with normal traffic, where features of malicious traffic are extracted and a classifier to detect malicious traffic is designed. In this paper, we propose an outline of the designing classifier using traffic between infected PCs and C&C server or traffic to download malwares. Simulation results are also described using CCC DATA Set 2009.
Manuscript in PDF(Japanese) |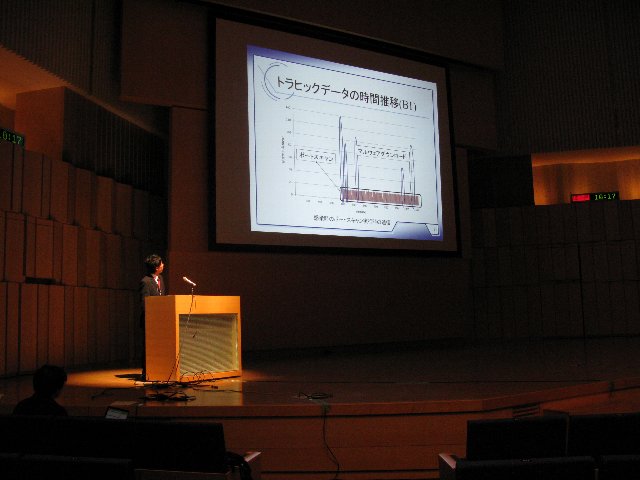
A5-3: Kazuya Kuwabara, Heuristics for Detecting Types of Infections from Captured Packets
In dynamic analysis of malware, preprocessing of communication data is effective to extract communication data with specific feature.In this paper,we describe database for storing meta data extracted from communication data for malware analysis.We can select communication data with specific feature by using this database,and it is expected to enhance productivity of researches on dynamic analysis.We tested the effectiveness of this method by applying it to CCC DATAset 2009.
Manuscript in PDF(Japanese) |
A5-4: Yoshiki Higashikado, Study for Detecting C&C Communication Based on Behavior of TCP/IP Session
This paper studies the analysis on the CCC Data Set 2009 for behavior of downloads of the malware and the port-scans .The analyses show that some new features of the single and the federated infections.Based on the analysis, the paper proposes heuristic techniques for detection of malwares infection and reports the accuracy of the proposed heuristics.
Manuscript in PDF(Japanese) |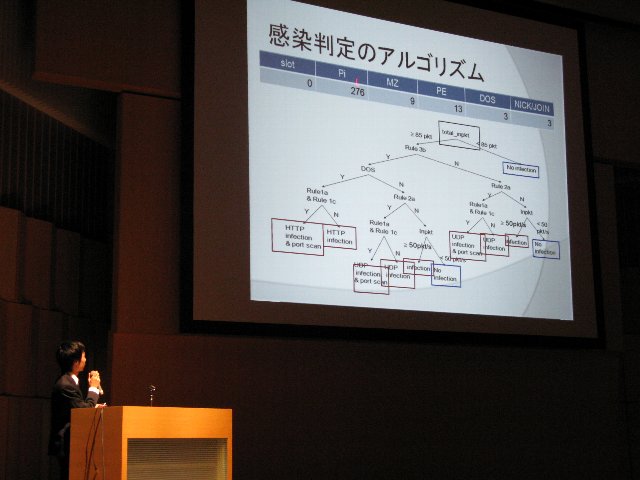
A5-5: Keisuke TAKEMORI, Network-based Prevention against Malware Communications
The command and control communication(C&C communication) is used for attacker to manage the behavior of their bots. To identify these communications is very important for examining the method of decreasing the harmful bots damage. In this paper, the detection method of the C&C communication is described. The method was obtained by analyzing the attack communication data of CCC DATAset 2009. It was possible to apply to various bots, and it was able to specify the C&C communication by short odds of almost 100%.
Manuscript in PDF(Japanese) |
A malware infected host receives command & control packets and new malware code from malicious servers. The infected hosts send spam mail messages via internet mail servers. A malware communication scenario is defined by a state machine that is composed of malicious packets. When the communication scenario is blocked by a router, it is expected that communication activities of the malware are restrained. In this research, we investigate both the malicious packets and the communication scenario using the CCC DATAset 2009 attack communication data, and propose a network-based prevention technique against the malware communication. Also, we apply the prevention technique to a test-bed network that monitors the malware packets and communication scenario. As the suppression level of the malware communication is evaluated, the effective prevention technique is demonstrated using the CCC DATAset 2009 malware code.
Manuscript in PDF(Japanese) |
A4-2: Junya Kato, Detection method of malware activity based on the Firewall log
Malware distribution hosts has various kind of characteristics such as active period or traffic pattern. Early detection of malware distribution hosts that distribute unknown malwares is important for effective countermeasure of outbreak of them. In this paper, based on CCC DATAset 2008 and 2009, we analyze attack source data and attack traffic data, and show characteristics of malware distribution hosts which is effective for early detection of potential threat.
Manuscript in PDF(Japanese) |
A4-3: Yoshiyuki SEINO, Traffic Visualization for Malware Analysis
Today, the wide-scale malware spread and DoS attacks often affect the availability of network systems and cause the system overflow, and threat the continuity of companies. In this research, we have investigated the method to detect the malware activity like DoS attacks and infection spread, by focusing on the practical aspects of the security operations and using the firewall log which has the high diffusion rate in the security products. As a result, we have found that it is helpful to monitor the patterns which comply with the specific condition of the firewall log to identify the malware activity.
Manuscript in PDF(Japanese) |
A4-4: Junichi Ikeda, Visualizing and Detecting Bot Activities by Time-series Analysis of Network Traffic
In recent years, serious damages by the malware’s activities on Internet are increasing. The malware analysis is required to prevent from the malware propagation. It is a set for the malware analysis to observe the malware’s characteristic traffic. We developed an analysis tool that visualizes destination IP Address. This tool can show the transmission status as an animation from the Honeynet data. By using this tool, we efficiently display a lot of connections on movie, and easily discover the malware’s characteristic traffic.
Manuscript in PDF(Japanese) |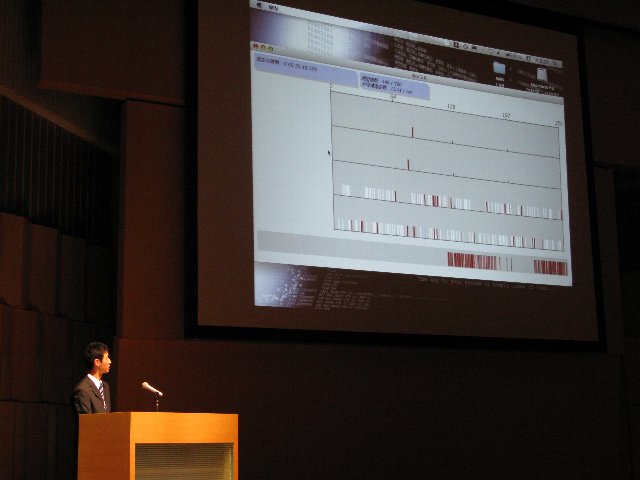
The purpose of this study is taking measure of bot net by understanding the characteristic and the tendency to the bot communication. We used the attack communication data of CCC DATASet 2009 on time-series analysis of the other party of the communication of an infected terminal with bot. From the results of the experiments, we understood to identify typical bot activities from the network traffic.
Manuscript in PDF(Japanese) |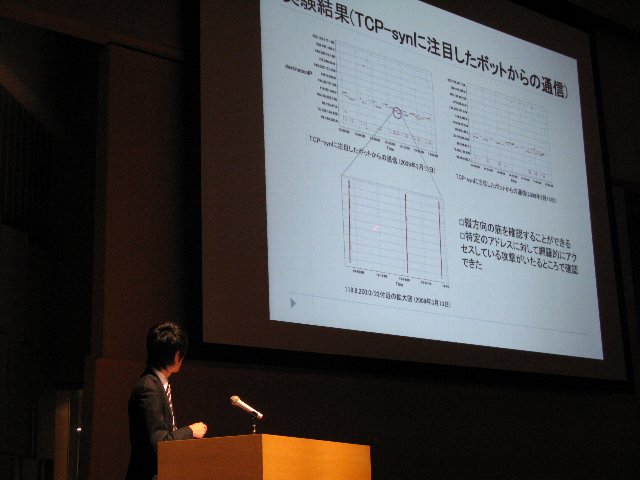
MOEKKO network team

Tokai University Human-wave tactics team

Internet Security Center team

Secureware team

Malware Walker team

Tokyo Denki University Mihara team
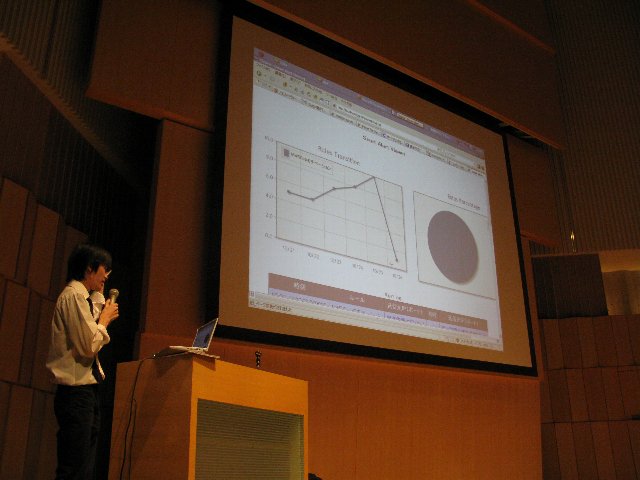
Team IIJ Motor Vehicles sig

A2-2: Tadaaki Nagao, A study of malware countermeasures based on a comparison between observations from honeypot networks of different sizes
In this study, we propose a new method to extract independent botnets from the CCC DATAset 2009, the log of downloading servers observed by distributed honeypots, by applying a technique of principal component analysis. The main results include that four independent botnets are distinguished and a year is divided into five phases.
Manuscript in PDF(Japanese) |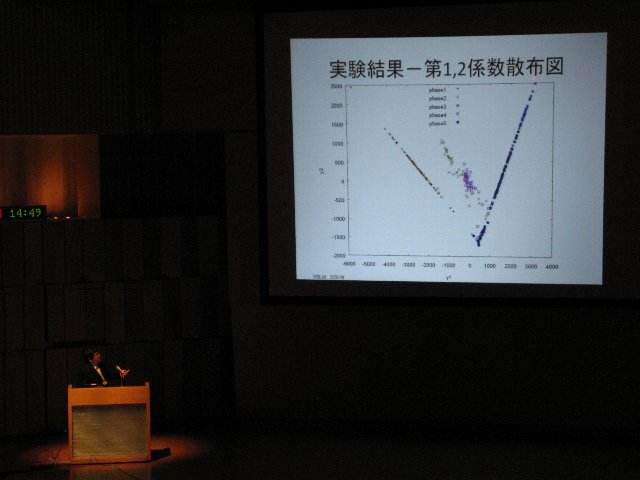
A2-3: Masayuki Ohrui, Mining Association rules consisting of Download Servers from Distributed Honeypot Observation
In this paper, we compare two observational data sets of malware infection activities, one of which is CCC DATAset 2009 Attack Source Data from wide honeypot network and another data set from IIJ's locally installed honeypot network. We study and discuss differences observed between them, and moreover, we also discuss countermeasures against infection activities.
Manuscript in PDF(Japanese) |
A2-4: Toshiaki Sudoh, Examination of attack generation and damage forecast system by multi point decentralized honeypot
This paper aims to find interested association rules, known as data mining technique, out of the dataset of downloading logs by focusing on the coordinated activity between downloading servers for malware. The result of the analysis shows the association rules of the relation among the downloading servers and that of the malwares.
Manuscript in PDF(Japanese) |
The vulnerability search and the attack activity were able to be often done to the entire Internet covering it, and to catch the situation of the entire Internet even with a small-scale sensing system several years ago. However, Internet Protocol address to be attacked for the evasion of detection and the improvement of the efficiency of the attack, etc. becomes limited in recent years and many of problems that occur on the Internet cannot be detected with a small-scale sensing system. In this text, a more efficient infection forecast system is examined by identifying the attack that pays attention to the communication property of each specimen material by using the data collected with two or more honey pot systems, considering the influence level, and combining the specimen material detection situations by differences between AS and Internet Protocol address, etc.
Manuscript in PDF(Japanese) |
A1-1: Mitsuhiro Hatada, Dataset for anti-malware research and research achievements shared at the workshop
A1-2: Takahiro Matsuki, Visualization of the Malware distribution by CCC DATAset 2009
There has been a lot of research on prevention, detection, protection and recovery against the complicated threats by malware. However, objective evaluation is likely to be hard because each evaluation data was made in their own way such as collecting by their original honeypot and its operation. This paper describes CCC DATAset 2008, a dataset for recent anti-malware research, and research achievements shared at MWS 2008. Furthermore, CCC DATAset 2009 for MWS 2009 and the requirements of dataset are outlined.
Manuscript in PDF(Japanese) |
A1-3: Fumihiko KOZAKURA, Visualization of malware attacks based on their sequences
The domestic BOTs infection decreases by continuation of the attention by the Cyber Clean Center. However, most undetectable malware are distributed from foreign countries. In this paper, promote the grasp of the actual situation by making the geographical distribution of the malware distribution visible with CCC DATAset 2009. Also downloader and infection to plural malware are increasing recently. Because make a URL list of the distribution of the malware and examine a method to prevent infection expansion with the downloader.
Manuscript in PDF(Japanese) |
From the attack host log of CCC DATAset 2009, we investigate the sequential relations among malwares and visualize the relations to clarify the trends of chain infections.
Manuscript in PDF(Japanese) |
July 31, 2009
June 18, 2009
MWS2009, 3rd interim meeting 
April 28, 2009
MWS2009, 2nd interim meeting
MWS2009, 1st interim meeting