MWS2011
October 19 - 21, 2011
[ "Photo story of MWS 2011", Manuscripts and Slides ]
These manuscripts have been published without reviewing and editing as received from the authors: posting the manuscript to MWS2011 does not prevent future submissions to any journals or conferences with proceedings.

 TOKI MESSE; Niigata Convention Center, Niigata, Japan |
Award ceremony 1A1: Malware samples (1) 1A2: Malware samples (2) 2A1: Access Log 2A2: Captured Data 2A4: D3M MWS Cup 2011 |
Award ceremony
1A1: Malware samples (1)
Datasets for Anti-Malware Research - MWS 2010 Datasets -
Mitsuhiro Hatada (NTT Communications Corporation), You Nakatsuru (Japan Computer Emergency Response Team Coordination Center) and Mitsuaki Akiyama (NTT Information Sharing Platform Laboratories) | |
There has been a lot of researches on countermeasures against the complicated threats by malware. anti-Malware engineering WorkShop (MWS) were held annually (2008 - 2010) in order to evaluate the proposals objectively and share the research achievements by using CCC DATAset 2008 - 2010. This paper presents an overview of MWS 2011 Datasets for MWS 2011: CCC DATAset 2011 and D3M 2011. [ Manuscript (PDF) | Slide (PDF) ] |

|
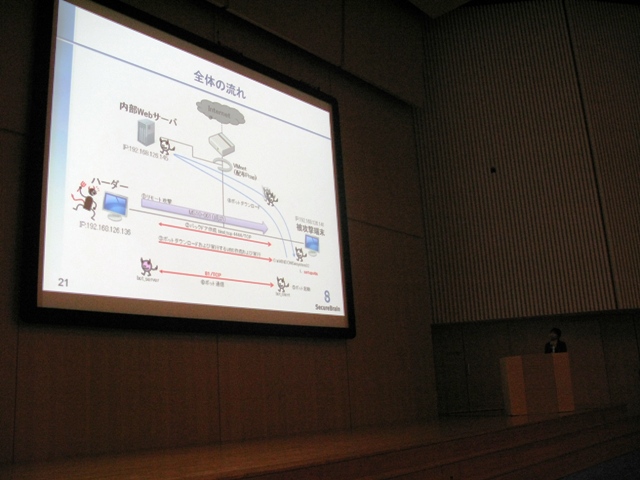
Automatic Detection and Removal of Malware in CCC DATASet 2011 using Anti-Malware User Support System
Nobutaka Kawaguchi, Takayuki Yoda, Hiroki Yamaguchi, Masato Terada (Hitachi Ltd.), Toshihiko Kasagi (KDDI Corporation), Yuji Hoshizawa (Securebrain Corporation), Masashi Eto, Daisuke Inoue and Koji Nakao (National Institute of Information and Communication Technology), | |
The authors have been developing Anti-Malware User Support System, which analyzes suspicious programs installed on users' PCs by employing dynamic malware analysis systems and automatically removes detected malicious programs. In addition to removing the malicious programs, this system can remove/repair files and registries that the malicious programs created/modified by generating removal tools based on behavior analysis reports obtained from the dynamic malware analysis systems. In this paper, we will show how this system analyzes and removes malware in CCC DATASet 2011. [ Manuscript (PDF) | Slide (PDF) ] |

|
Speci ying the Addresses of IAT Entries
Makoto Iwamura, Yuhei Kawakoya and Takeo Hariu (NTT Information Sharing Platform Laboratories) | |
We propose a novel approach, which accurately specifies the addresses of Import Address Table (IAT) entries in unpacked malware. Existing approaches specify the IAT entry addresses by finding the machine code instructions that uses an IAT entry in the result of disassembly. However, since a compiler for Windows tends to output a binary mixing variable length instructions and data, it is difficult to correctly disassemble unpacked malware. For solving the problem, our approach calculates the probabilities that each address in malware points to an IAT entry, and then finds highly probable IAT entry addresses. [ Manuscript (PDF) | Slide (PDF) ] |

|
Dynamic Packer Identification Based on Instruction Trace
Yuhei Kawakoya, Makoto Iwamura and Takeo Hariu (NTT Information Sharing Platform Laboratories) | |
Most of the malware in the real world is obfuscated by a packer which is designed for disturbing static analysis. In order to analyze such malware, we first have to unpack the malware and extract the original code from it. The obfuscation algorithm is different for each type of packer so it is better to take a different approach suited for each packer type. However, the fact that a large number of different types of packers exist makes it difficult to correctly identify the type of packer by signature-based identification, which is a common existing method. So, in this paper, we propose a dynamic packer identification method, which executes malware in an isolated environment, collects instruction trace logs, and compares them with signatures of packer-specific instruction sets. Identifying the types of packers and understanding their packing algorithm allow us to effectively unpack obfuscated malware. To evaluate our proposed method, we have conducted a cross validation against 80 sample executables which are generated by packing 8 standard Windows executables with 10 common packers. As a result, we succeeded to identify the types of packers for all 80 executables. Lastly, we show the result of the experiment with CCC Dataset 2011. [ Manuscript (PDF) | Slide (PDF) ] |

|
1A2: Malware samples (2)
A Method to Get Result of System Calls for Malware Analysis
Yuto Otsuki, Eiji Takimoto, Takehiro Kashiyama and Koichi Mouri (Ritsumeikan University) | |
Recent malwares are applied anti-debugging techniques not to be analyzed by dynamic analysis tools. We are developing "Alkanet" that is an extension for malware analysis in virtual machine monitor. Virtual machine monitor runs higher privilege level than malware. Therefore, malware's anti-debugging techniques are ineffective against Alkanet. Alkanet monitors behavior of malwares by a system call invoked by processes or threads on guest OS. The behavior of malwares is analyzed by getting result and arguments of the system calls. Furthermore, Alkanet extracts details of malware behavior from the system call log. [ Manuscript (PDF) | Slide (PDF) ] |

|
Faster analysis of malware log using Knuth Bendix completion algorithm
Ruo Ando and Shinsuke Miwa (National Institute of Information and Communication Technology) | |
In this paper we propose a faster log processing method for analyzing malware using knuth bendix completion algorithm. Diversified log string of malware is translated into a representation of FoL (First order Logic) formulation and resolved to discover hidden behavior of malware. Besides, we apply reasoning stragety for term rewriting called as knuth bendix completion algorithm for ensuring termination and confluency. Knuth bendix completion includes some inference rules such as lrpo (the lexicographic recursive path ordering) and dynamic demodulation. Proposed system enables us to fasten reasoning process and assure the termination and confluent analysis. [ Manuscript (PDF) | Slide (PDF) ] |

|
Consideration on Malware Classification by the Function based on the Malware's Code
Yuka Higashi (Nara Institute of Science and Technology), You Nakatsuru (Little eArth Corporation Co., Ltd), Atsuo Inomata (Nara Institute of Science and Technology), Hideki Sunahara (Keio University) and Kazutoshi Fujikawa (Nara Institute of Science and Technology) | |
Recently various kinds of security incidents occur and what is more the majority of attacks in such the incidents have been used Malware, there is an urgent need to analysis and measures against for unknown future Malware. Some of the static analysis of malware are suitable for understanding their behavior, however it needs more skills and more times. In this paper, we compare a method of calculation from the function with method of complete Malware code. Furtheremore we explore the relationship between function code and degree of its similarity. [ Manuscript (PDF) | Slide (PDF) ] |
|
About Malware samples of CCC DATAset 2011
Kiyotaka Miyazaki (Japan Computer Emergency Response Team Coordination Center) | |

|
|
2A1: Access Log
Consideration of security problem to assume the IPv6 Internet to be attack route
Toshiaki Sudoh (Internet Mulifeed Corporation) | |
It became "IPv4 address dryness" in which the IPv4 address that was able to be the allotment became out of stock by usual application in Asia Pacific region including Japan in April, 2011. The communication environment under which IPv6 can be used as it becomes possible for the IPv6 correspondence to proceed by various services along with it, and to use the IPv6 address by the standard even in the access line service for the average user begins to be maintained. The change in such an electronic environment influences the security problems such as the fishing, spam, and the malware infection. In this text, the relativity of the attack communication data of attack data and MWS2011 DATAset of which the attack route is the IPv6 Internet is analyzed, and the current state of the attack using the IPv6 net and the influence in the future are analyzed. [ Manuscript (PDF) | Slide (PDF) ] |

|
Integrate analysis malware from geographic visualization
Hirokazu Kaneko (LAC Holdings, Inc.) | |
Cyber attacks use several methods and threaten social infrastracture. Especially, malware is highly sophisticated to steal more valuable information, and the victimes are not aware of it's infection. Thus, it is difficult to detect and distinct malware infections by physical sence. In this paper, we geographical visualize malware's attack point with CCC DATAset 2011's Attack-Connection Data and Attack-Source Data, and creates support system for integrate analysis malware to obvious attacker's purpose. [ Manuscript (PDF) | Slide (PDF) ] |

|
Correlation Analysis Between IP Addresses Used in Variety of Attacks
Daiki Chiba (Waseda University), Takeshi Yagi, Mitsuaki Akiyama (NTT Information Sharing Platform Laboratories), Tatsuya Mori (NTT Service Integration Laboratories) and Shigeki Goto (Waseda University) | |
Malware now attacks not only vulnerabilities in the Windows operating system, but also those of web applications on servers and web browsers on personal computers. To collect attack information for protective use, many types of honeypots have been developed. However, attack information that can be collected by each type of honeypot is limited, so it is necessary to collect it more efficiently. Our proposal performs correlation analysis of IP address structures in attack data collected by various types of honeypots, and detects IP addresses of attackers which are used for various attacks. Using IP addresses allows us to detect certain types of malware infection attacks efficiently. [ Manuscript (PDF) | Slide (PDF) ] |
|
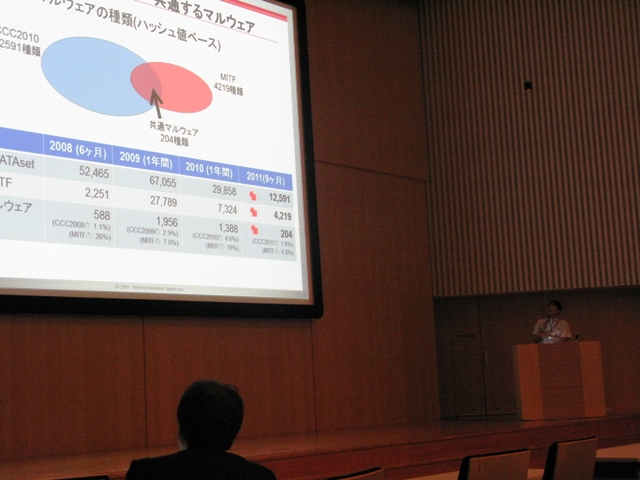
A study of malware countermeasures and an analysis of malware behavior based on observations from two honeypot networks of different sizes
Tadaaki Nagao, Hiroshi Suzuki, Masahiko Katoh and Mamoru Saito (Internet Initiative Japan Inc.) | |
In this paper, we compare two observational data sets of malware infection activities, one of which is CCC DATAset 2011 Attack Source Data from Cyber Clean Center’s wide honeypot network and another from IIJ’s locally installed honeypot network. We study and discuss differences observed between them, and moreover, we also discuss countermeasures against infection activities. [ Manuscript (PDF) | Slide (PDF) ] |
|
2A2: Captured Data
Development of Bot Communication Detection Method Using Snort Rules and Its Use to Extend DICE (Defaced Sites Automatic Detection System)
Tatsuya Tanaka and Ryoichi Sasaki (Tokyo Denki University) | |
Botnets are expanding the scale by infecting the malware on PC and spreading damage. As a way to infect the malware, there exist attacks from Web page and unauthorized intrusion. In order to use IDS for detecting unauthorized intrusion, big amounts of Rule set of IDS must be tuned to be suitable to the required environment. In this paper, we analyze CCC DATAset 2011 using Snort and extract best rules of Snort and validate the best rules among them. In addition, we proposed a method to prevent infection caused by not only web pages attack but unauthorized intrusion by using the rules to expand the function of DICE (Defaced Sites Automatic Detection System). [ Manuscript (PDF) | Slide (PDF) ] |

|
A Combined Machine Learning Method for Sustainable Detection of Attacks
Hiroaka Kokubo (University of Tsukuba), Masahiro Mambo (Kanazawa University) and Eiji Okamoto (University of Tsukuba) | |
Recently, the malware proliferation rate is highest ever and unknown malware appears frequently. Therefore, it is necessary to detect the invasion and the activity of unknown malware, and to prevent damage. In this paper, we combine multiple machine learning methods to achieve sustainable detection of attack communication including unknown attacks. We use the attack communication data of the CCCDATAset2011 for the analysis of the proposed method. [ Manuscript (PDF) | Slide (PDF) ] |

|
A study of feature evaluation considering effects of year for malware detection
Kenji Kawamoto, Tatsuya Ichida (Waseda University), Masatsugu Ichino (The University of Electro-Communications), Mitsuhiro Hatada (NTT Communications Corporation) and Naohisa Komatsu (Waseda University) | |
In this paper, we evaluated features used in existing researches based on the experiment that showed how each features could discriminate anomaly traffic that was infected with malware from normal traffic that was not infected with malware. In this evaluation, we made discriminations using the distance between the normal or anomaly codebook made by each features using vector quantization and test data. In this paper, we used CCCDATAset as anomaly traffic data, some traffic data on an intranet which was the same date as anomaly traffic data as normal traffic. Then we report our consideration which features are effective for malware detection with no relation to year effects. [ Manuscript (PDF) | Slide (PDF) ] |

|
A study on malware detection method using time series traffic data
Masatsugu Ichino (The University of Electro-Communications), Tatsuya Ichida (Waseda University), Mitsuhiro Hatada (NTT Communications Corporation) and Naohisa Komatsu (Waseda University) | |
We propose a method of malware detection method using time series traffic data. Damage by malware attack has been viewed with suspicion recently. We studied the malware detection method by comparing malware traffic with normal traffic. So we design the classifier to identify malware traffic. We use the AdaBoost as a classification algorithm considering practicability and study a method of malware detection method using time series traffic data. In this paper, we evaluated the effectiveness of proposed method by using CCCDATASet. [ Manuscript (PDF) | Slide (PDF) ] |

|
Investigation on Technical Requirements toward Open Distribution of Honeypot Trace Data for Information Security Research
Takurou Hosoi and Kanta Matsuura (The University of Tokyo) | |
Traffic data (traces) which are used in network security researches potentially contain privacy information and hazardous data, so most of them are only used privately, which hinders third-party verification of their results and promotion of their relating researches. In this research, we investigated technical requirements for honeypot traces, such as ones included in the common research dataset CCC DATAset 2011, toward their open distribution for information security researches regarding their security and usefullness. We also tried to detect suspicious host location identification traffic from Attack Traffic Data of CCC DATAset 2011 by simple easy ways as a first step. [ Manuscript (PDF) | Slide (PDF) ] |

|
2A4: D3M
Evaluation of Technique to Detect C&C Server of Botnet Using Accumulated Data
Nobuhiro Nakamura and Ryoichi Sasaki (Tokyo Denki University) | |
Recently, the damage caused by the botnet has been increasing. There exists a problem that the other bot PCs can be produced, even if one bot PC could be specified and removed.Therefore, we proposed the Multi Stage Trace Back system. We also developed second stage trace back method which consists of black list and Quantification methods No. 2 with CCCDataSet2009 and CCCDataSet2010.This paper reports the evaluated results of applying Quantification methods No. 2 with CCCDataSet2011 and accumulated of the three years minute. [ Manuscript (PDF) | Slide (PDF) ] |

|
A consideration for categorizing Javascript files based on Abstract Syntax Tree Fingerprinting
Daisuke Miyamoto (The University of Tokyo), Gregory Blanc (Nara Advanced Institute of Science and Technology) and Mitsuaki Akiyama (NTT Information Sharing Platform Laboratories) | |
In this paper, we discuss a classification method for obfuscated Javascript source codes. Recently, malicious webpages often employs obfuscation techniques based on Javascript to make it difficult to analyze the threat. This paper focuses on identifying the types of obfuscation techniques, rather than decoding the obfuscated code. Our proposed method uses Abstract Syntax Tree(AST), which is designed for detecting the similarity of multiple source code. We employ Chilowicz's AST Fingerprinting as a metric of the similarity, compare and categorize source codes extracted from MWS research dataset, and show the results of our analysis. [ Manuscript (PDF) | Slide (PDF) ] |

|
Identifying Characteristic Syntactic Structures in Obfuscated Scripts by Subtree Matching
Gregory Blanc (Nara Advanced Institute of Science and Technology), Mitsuaki Akiyama (NTT Information Sharing Platform Laboratories), Daisuke Miyamoto (The University of Tokyo) and Youki Kadobayashi (Nara Advanced Institute of Science and Technology) | |
Many approaches to web malware detection tend to consider obfuscated scripts as malicious, although it is has been demonstrated that obfuscator does not indicate malice. In a bid to distinguish obfuscation techniques used in malicious and benign scripts, we propose a subtree matching technique to identify learned structural patterns in analyzed scripts. Our proposal implements two techniques from the realm of natural language processing and string algorithms. We advocate the use of abstract syntax trees to reduce the entropy introduced by string randomization and rather focus on code structure patterns. In a learning phase, we discover frequently occurring trees in abstract syntax treebanks, while in the testing phase, we attempt to identify these trees within a candidate AST by using a pushdown automata that accepts the set of learned trees. [ Manuscript (PDF) | Slide (PDF) ] |

|
Categorizing Hostile JavaScript using Abstract Syntax Tree Analysis
Masaki Kamizono, Masata Nishida, Emi Kojima and Yuji Hoshizawa(Securebrain Corporation) | |
In the recent years, many hostile websites have been using polymorphic JavaScript in order to conceal its code. The author of this article had previously proposed and developed a system based on dynamic analysis to process and detect such types of JavaScript. However, a challenge often encountered with that approach is the mandatory preparation of very detail-oriented environments that may also require specific user-driven events for the hostile JavaScript to execute properly as it was designed to. As an alternative solution, this paper will propose the use of an abstract syntax tree based on structural analysis of polymorphic JavaScript to detect and categorize hostile JavaScript. This paper will also elaborate on test results based on the proposed algorithm. [ Manuscript (PDF) | Slide (PDF) ] |

|
MWS Cup 2011
Technical Component (90 minutes)

Artistic Component (each 3 minutes)
|
Team GOTO Love |

|
|
24Droid |

|
|
Retry=1 |

|
|
Publish press release After award winner. IIJ, Office of Emergency Response and Clearinghouse for Security Information |

|
|
Revenger |

|
|
Tokyo Denki University ISL |

|
Venues (Main hall)
|
Reviewers of Artistic Component |

|

|
Speech of Reviewer Chair |